Recent Content:
I am proud to announce the release of it-depends, an open-source tool for automatic enumeration of dependencies. You simply point it to a source code repository, and it will build a graph with the required dependencies. It-depends currently supports cargo, npm, pip, go, CMake, and autotools codebases, packages in their associated package managers, and Ubuntu apt.
I recently created a challenge for the justCTF competition titled PDF is broken, and so is this file. It demonstrates some of the PDF file format’s idiosyncrasies in a bit of an unusual steganographic puzzle. CTF challenges that amount to finding a steganographic needle in a haystack are rarely enlightening, let alone enjoyable. LiveOverflow recently had an excellent video on file format tricks and concludes with a similar sentiment. Therefore, I designed this challenge to teach justCTF participants some PDF tricks and how some of the open source tools I’ve helped develop can make easy work of these forensic challenges.
Read the full post on the Trail of Bits blog for spoilers on how to solve the puzzle.
Note: My advice is specifically related to the higher education system in the US; other countries have very different systems. My advice is also solely based on experience in the field of Computer Science; this may translate to other STEM fields, but certainly not all academic fields.
Do you really want a Ph.D.?
Make sure you are doing this for the right reasons!
Reasons to get a Ph.D.
- You want to work in academia. If you want to get a tenure track research position at a university, you need a Ph.D.
- You need it to get a promotion at work. This is typically only true at larger corporations, where having certain credentials is necessary to progress through the ranks.
- You enjoy being in an academic environment and solely want the experience. This is perfectly valid. Being in grad school can (but isn’t guaranteed to) be incredibly invigorating.
Reasons not to get a Ph.D.
Dat Phizzle Dizzle Doh
The novelty of putting those letters after your name and/or being called “Doctor” wears off real quick.You just want to teach at a university
Universities are really hungry for adjunct professors these days. You usually don’t need a Ph.D. to teach. Try teaching a class or two before you commit to getting a Ph.D. and making that your career. I’ve taught a bunch of classes, both at the undergraduate and graduate levels, including developing the entire syllabus, assignments, and slides all from scratch. It is a lot of work, and usually not worth what they pay you.You want to work on your dissertation topic for the rest of your career
I know dozens, maybe hundreds of Ph.D.s, and I can count on one hand the number of people who continued research related to their dissertation topic after graduation.Imposter Syndrome
I’ve worked with plenty of people with no degree who are far more capable than people with multiple grad degrees.You’re probably not going to get a job in academia
I know several people who got Ph.D.s from top tier schools like CMU and MIT and all of them either ended up in industry or teaching at small liberal arts schools with no graduate program (because they were dead set on ascending the ivory tower). The academic market is super tough, and will only get tougher thanks to the inevitable closure of smaller schools and a general preference for adjuncts over tenure-track professors. Ph.D. programs do not limit the number of students they accept based on the anticipated number of professorial job openings. There are many more Ph.D.s than professorships!Even if you do get your dream job in academia, you’ll probably hate it and/or lose it
I don’t think I know of a single professor, tenured or otherwise, who loves their job. They need to take on a huge teaching load thanks to the dearth of adjuncts and/or assume administrative positions that do not incur an increased salary.The financial implications and opportunity cost of leaving your job for three to ten years
Some studies have concluded that getting a Ph.D. will require up to fifty years to outweigh the opportunity cost of staying in the workforce and advancing your career. But in some circumstances it can be as few as five years. This is because there is a lot of variance in the compensation for graduate students. Be prepared for three to ten years of significantly reduced income.The Snake Fight
Beware.Common reasons you will fail
There are myriad reasons why you might fail to complete your Ph.D. that are almost all completely out of your control.Survivor bias is real. Trust me, I’m a survivor.
Only two out of the ~dozen students in my research lab ever completed their degree. Keep that in mind when you take advice from the survivors.Someone “scoops” your research
This is typically more of an issue in the more theoretical specializations, but it does happen. If someone solves your problem before you, you’ve got to start over. I’ve written an essay about this.Your advisor switches schools
Sometimes this can be a good thing; for example, a friend of mine’s advisor transferred from an average school to MIT right before my friend graduated, and he was able to transfer over all of his credits, defend at MIT, and get MIT on his diploma. But I also know a bunch of people who were bitten by this, where the new school would not accept their credits and/or there was no funding at the new school for tuition remission and a stipend, so they basically had to drop out.Your advisor goes on sabbatical
It’s hard to be advised if your advisor is off galavanting for a year or two. Good advisors plan for this, but I know of several cases where students had to drop out because their advisor didn’t plan ahead.You don’t get along with your advisor, or they go AWOL, or their tenure application is denied, (or they die)
Ever look at a 101-level STEM textbook? There are usually at least two authors: The one who knows what they’re talking about, and the one who speaks English as a native language. I had two advisors for basically the same reason. My first advisor had lots of research grants and contracts which afforded me tuition remission and a good stipend. But that work was mostly applied science; nothing was deep enough to turn into a thesis topic. So I took on a co-advisor who had just been hired as a new tenure-track professor and was full of cool ideas. A few months later he unfortunately, suddenly, died. Then I took on a third co-advisor (who was happy to take me on because he didn’t have to worry about paying me from his own grants). This amounted to more work for me, since I had to do the work to “pay the bills” with my original advisor as well as my actual research with my new co-advisor. But it also gave me a bunch of freedom to just work on what I wanted. With that said, I had two labmates who were working under my late co-advisor who were unable to find a place for themselves after his death, and never completed their dissertations. A lot of it is luck. If a professor’s tenure application is denied, they are usually given a year to wrap up their business and leave the school. Most departments have contingency plans to pair orphaned graduate students with new advisors, but this can be a devastating blow to most students, for all intents and purposes similar to their passing away.You don’t have enough time to focus on your research
In my case, I was effectively working a full time job doing applied research for my first advisor in addition to being a “regular” graduate student with my co-advisor. This entailed 60+ hour work weeks for basically my entire Ph.D. It’s super hard to focus on research if you have a full time job; I only know of one or two people who successfully completed a part-time Ph.D. while working a full time job at the same time.You still want to get a Ph.D.?
Things you need to do before applying
Do you already have a master’s degree?
Some schools in the US do not require you to take any classes, while most others require you to effectively earn a Master’s in the process of getting your Ph.D. If you do not have a Master’s yet, try and choose a school that effectively forces you to earn a Master’s in the process of getting a Ph.D., as that will be a nice consolation prize in the event that you do not complete your dissertation. If you do have a Master’s, check on your prospective school’s degree requirements and whether they will accept your existing credits. If a school requires you to take a bunch of classes and you don’t want to earn a second Master’s, make sure they will waive that requirement for you. This affected me when I was deciding on which program to join, since I already had a Master’s and many schools wouldn’t budge on forcing me to re-do all of my Master’s classes.Decide in what you want to specialize
More on this below, but it’s best if you know what you want to research before you apply to a program. You don’t choose a school for a Ph.D. the same way you choose a school for an undergrad or even a Master’s degree. Choose the school based upon how your desired research aligns with what the professors there are doing, not based upon the name or prestige of the school.Read the entire Ph.D. Comics archive
Seriously, it’s really good, and completely accurate.How to get into a good program
Find potential advisors first
Compile a list of everyone who is actively doing research in an area related to your desired specialization. Send them an E-mail stating your desire to pursue a Ph.D. Ask them if they are taking on new students, and, if so, what their time frame is. The easiest way to get accepted to a Ph.D. program is to have a professor advocating on your behalf. If a professor wants to work with you, they can guide and even fast-track you through the admissions process.You should not have to pay your way through a Computer Science Ph.D.
Don’t expect to be rich, but every decent computer science Ph.D. program should offer tuition remission and a slightly-above-the-poverty-line stipend, either by acting as a teaching assistant (TA) or as a research assistant (RA). Do not accept any less. If the school wants you to pay for your Ph.D., something is wrong. Being an RA is preferable to a TA.Having a source of external funding lined up will get you into almost any school
The biggest limiting factor in taking on new students both at the departmental and professorial levels is funding. A professor will not advise a new student unless they have enough funding (either through grants/contracts that fund RA-ship, or through departmental TA-ships). If there are no TA openings and/or the professor doesn’t have enough grant funding to pay for your stipend and tuition remission, then they won’t take you on as a student. In such situations, you can either pay for your own tuition and forego a stipend (never, ever, do this!), or you can come to the table with your own external source of funding! This can be through a grant program (e.g., the NSF GRFP). If a professor doesn’t have to worry about how to “feed” you, they’ll be thrilled to work with you, and it will give you a lot more freedom in directing your own research.How to minimize your chances of failing
Talk to your potential advisor’s current and past students
Do this preferably before even applying. How many of the professor’s students actually graduate? Where do they end up after graduation? How many papers does each student publish per year? How is travel to conferences funded? What is the professor’s advising style like? This will vary drastically from professor to professor.
I’d be lucky to talk to one of my co-advisors once a month.
What is the professor’s advising style like? This will vary drastically from professor to professor.
I’d be lucky to talk to one of my co-advisors once a month.
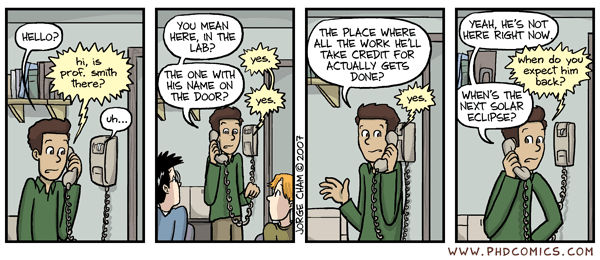 My other co-advisor would actually sit down with me 1-on-1 and we’d read aloud a new paper together,
sentence-by-sentence, ensuring that we each understood what was written before moving on. Some people might hate that,
though. Different styles work for different kinds of students. Some professors demand that you work on a specific
problem they have defined, whereas others expect you to carve out your research topic yourself. Determine what type of
advisor you think you need, and interview existing students to see if the professor meets your needs.
My other co-advisor would actually sit down with me 1-on-1 and we’d read aloud a new paper together,
sentence-by-sentence, ensuring that we each understood what was written before moving on. Some people might hate that,
though. Different styles work for different kinds of students. Some professors demand that you work on a specific
problem they have defined, whereas others expect you to carve out your research topic yourself. Determine what type of
advisor you think you need, and interview existing students to see if the professor meets your needs.
Interview your potential advisor in advance
What is a typical week in the life of an advisee like? How many regular meetings are there? How often do students typically meet with their advisor 1-on-1? Will the professor expect you to take any specific classes, regardless of the school’s degree requirements? Professors will often require you to take certain classes they think are really good. Is the professor planning to go on sabbatical any time soon? Do they have tenure? (Typically, professors will earn and usually take a sabbatical shortly after earning tenure. If a professor applies for tenure and is denied, they usually only get a year before they are fired. Some schools give professors two chances at getting tenure.) What is the professor’s teaching load like? Would they expect you to teach and/or TA? Or could you be an RA full time? What is their research grant pipeline like? When do their current grants end?Choose a topic that is unlikely to be “scooped”
I already linked to this above, but please read this essay I wrote. Try and choose a dissertation topic that can’t be duplicated by someone else first. This usually means choosing a topic that—even if it is inherently theoretical—could worst-case be “proven” empirically in the event that you can’t prove it formally.Remember that your dissertation is unlikely to ever be read by anyone other than your committee members
It is, in a sense, a rite of passage. If you don’t intend to go into academia, there is no shame in doing the minimum amount possible that can get you graduated. With that said, my dissertation is super awesome and you should totally read it right now. Plz, become the sixth person to have ever read it.
What to expect after you have a Ph.D.

Breaking into Google Headquarters
In which I tempt the criminal justice system while flaunting the California statute of limitations.

Over the past few years I’ve been a frequent contributor to and editor of the journal PoC or GTFO. Part of my contributions have been to help create several of the recent file polyglots for the electronic releases. I just presented a talk on this topic at BSides Philly, 2017.
A polyglot is a file that can be interpreted as multiple different filetypes depending on how it is parsed. While polyglots serve the noble purpose of being a nifty parlor trick, they also have much more nefarious uses, e.g., hiding malicious printer firmware inside a document that subverts a printer when printed, or a document that displays completely different content depending on which viewer opens it. This talk does a deep dive into the technical details of how to create such special files, using examples from some of the recent issues of the International Journal of PoC||GTFO. Learn how we made a PDF that is also a valid NES ROM that, when emulated, displays the MD5 sum of the PDF. Learn how we created a PDF that is also a valid PostScript document that, when printed to a PostScript printer, produces a completely different document. Oh, and the PostScript also prints your /etc/passwd file, for good measure. Learn how to create a PDF that is also a valid Git repository containing its own LaTeX source code and a copy of itself. And many more!
Here is a recording of the talk,
as well as my slide deck:
 PoC‖GTFO
PoC‖GTFO Twitter
Twitter LinkedIn
LinkedIn GitHub
GitHub XTerm
XTerm
 Esperanto
Esperanto
 עברית
עברית
 Medžuslovjansky
Medžuslovjansky
 Русский
Русский
 This is an excerpt from the
This is an excerpt from the 



